Generate X 509 Certificate From Private Key
Mar 03, 2020 Generating an RSA key with a self-signed X.509 certificate. If you're validating keys against registry-level certificates, the certificate must meet certain requirements. One of these requirements is that the certificate use the X.509 standard. To generate a 2048-bit RSA private key and a self-signed X.509 certificate with a SHA-256 signature. Create and sign an X509 certificate You can create an X509 certificate for your application with OpenSSL. OpenSSL is a standard, open source library that supports a wide range of cryptographic functions, including the creation and signing of x509 certificates. Steps for generating a certificate and private key for the RACF address space. Perform the following steps to generate an X.509 V3 certificate and associated private key, and prepare them for RACF use during the enveloping process. Generate a digital certificate containing a private key. Dec 11, 2016 Hi, x509 certificates are used widely by a lot of applications. Generating x509 certificates seem to be hard and rocket science, but it is not. We will generate a key named t1.key and then create a signing request from this key. After that, to sign our request we will generate a self-signed CA key and certificate. Vault's PKI secrets engine can dynamically generate X.509 certificates on demand. This allows services to acquire certificates without going through the usual manual process of generating a private key and Certificate Signing Request (CSR), submitting to a CA, and then waiting for the verification and signing process to complete. Perform the following steps to generate an X.509 V3 certificate and associated private key, and prepare them for RACF use during the enveloping process. Generate a digital certificate containing a private key for the RACF address space.
-->To make an X.509 certificate accessible to Windows Communication Foundation (WCF), application code must specify the certificate store name and location. In certain circumstances, the process identity must have access to the file that contains the private key associated with the X.509 certificate. To obtain the private key associated with an X.509 certificate in a certificate store, WCF must have permission to do so. By default, only the owner and the System account can access the private key of a certificate.
To make X.509 certificates accessible to WCF
Give the account under which WCF is running read access to the file that contains the private key associated with the X.509 certificate.
Determine whether WCF requires read access to the private key for the X.509 certificate.
The following table details whether a private key must be available when using an X.509 certificate.
X.509 certificate use Private key Digitally signing an outbound SOAP message. Yes Verifying the signature of an inbound SOAP message. No Encrypting an outbound SOAP message. No Decrypting an inbound SOAP message. Yes Determine the certificate store location and name in which the certificate is stored.
The certificate store in which the certificate is stored is specified either in application code or in configuration. For example, the following example specifies that the certificate is located in the
CurrentUsercertificate store namedMy.Determine where the private key for the certificate is located on the computer by using the FindPrivateKey tool.
The FindPrivateKey tool requires the certificate store name, certificate store location, and something that uniquely identifies the certificate. The tool accepts either the certificate's subject name or its thumbprint as a unique identifier. For more information about how to determine the thumbprint for a certificate, see How to: Retrieve the Thumbprint of a Certificate.
The following code example uses the FindPrivateKey tool to determine the location of the private key for a certificate in the
Mystore inCurrentUserwith a thumbprint of46 dd 0e 7a ed 0b 7a 31 9b 02 a3 a0 43 7a d8 3f 60 40 92 9d.Determine the account that WCF is running under. The witcher product key generator.
The following table details the account under which WCF is running for a given scenario.
Scenario Process identity Client (console or WinForms application). Currently logged in user. Service that is self-hosted. Currently logged in user. Service that is hosted in IIS 6.0 (Windows Server 2003) or IIS 7.0 (Windows Vista). NETWORK SERVICE Service that is hosted in IIS 5.X (Windows XP). Controlled by the <processModel>element in the Machine.config file. The default account is ASPNET.Grant read access to the file that contains the private key to the account that WCF is running under, using a tool such as icacls.exe.
The following code example edits the discretionary access control list (DACL) for the specified file to grant the NETWORK SERVICE account read (:R) access to the file.
See also
 -->
-->A Key Vault (KV) certificate can be either created or imported into a key vault. When a KV certificate is created the private key is created inside the key vault and never exposed to certificate owner. The following are ways to create a certificate in Key Vault:
Create a self-signed certificate: This will create a public-private key pair and associate it with a certificate. The certificate will be signed by its own key.
Create a new certificate manually: This will create a public-private key pair and generate an X.509 certificate signing request. The signing request can be signed by your registration authority or certification authority. The signed x509 certificate can be merged with the pending key pair to complete the KV certificate in Key Vault. Although this method requires more steps, it does provide you with greater security because the private key is created in and restricted to Key Vault. This is explained in the diagram below.
The following descriptions correspond to the green lettered steps in the preceding diagram.
- In the diagram above, your application is creating a certificate which internally begins by creating a key in your key vault.
- Key Vault returns to your application a Certificate Signing Request (CSR)
- Your application passes the CSR to your chosen CA.
- Your chosen CA responds with an X509 Certificate.
- Your application completes the new certificate creation with a merger of the X509 Certificate from your CA.
- Create a certificate with a known issuer provider: This method requires you to do a one-time task of creating an issuer object. Once an issuer object is created in you key vault, its name can be referenced in the policy of the KV certificate. A request to create such a KV certificate will create a key pair in the vault and communicate with the issuer provider service using the information in the referenced issuer object to get an x509 certificate. The x509 certificate is retrieved from the issuer service and is merged with the key pair to complete the KV certificate creation.
The following descriptions correspond to the green lettered steps in the preceding diagram.
- In the diagram above, your application is creating a certificate which internally begins by creating a key in your key vault.
- Key Vault sends an TLS/SSL Certificate Request to the CA.
- Your application polls, in a loop and wait process, for your Key Vault for certificate completion. The certificate creation is complete when Key Vault receives the CA’s response with x509 certificate.
- The CA responds to Key Vault's TLS/SSL Certificate Request with an TLS/SSL X.509 certificate.
- Your new certificate creation completes with the merger of the TLS/SSL X.509 certificate for the CA.
Asynchronous process
KV certificate creation is an asynchronous process. This operation will create a KV certificate request and return an http status code of 202 (Accepted). The status of the request can be tracked by polling the pending object created by this operation. The full URI of the pending object is returned in the LOCATION header.
When a request to create a KV certificate completes, the status of the pending object will change to “completed” from “inprogress”, and a new version of the KV certificate will be created. This will become the current version.
First creation
When a KV certificate is created for the first time, an addressable key and secret is also created with the same name as that of the certificate. If the name is already in use, then the operation will fail with an http status code of 409 (conflict).The addressable key and secret get their attributes from the KV certificate attributes. The addressable key and secret created this way are marked as managed keys and secrets, whose lifetime is managed by Key Vault. Managed keys and secrets are read-only. Note: If a KV certificate expires or is disabled, the corresponding key and secret will become inoperable.
If this is the first operation to create a KV certificate then a policy is required. A policy can also be supplied with successive create operations to replace the policy resource. If a policy is not supplied, then the policy resource on the service is used to create a next version of KV certificate. Note that while a request to create a next version is in progress, the current KV certificate, and corresponding addressable key and secret, remain unchanged.
Self-issued certificate
To create a self-issued certificate, set the issuer name as 'Self' in the certificate policy as shown in following snippet from certificate policy.
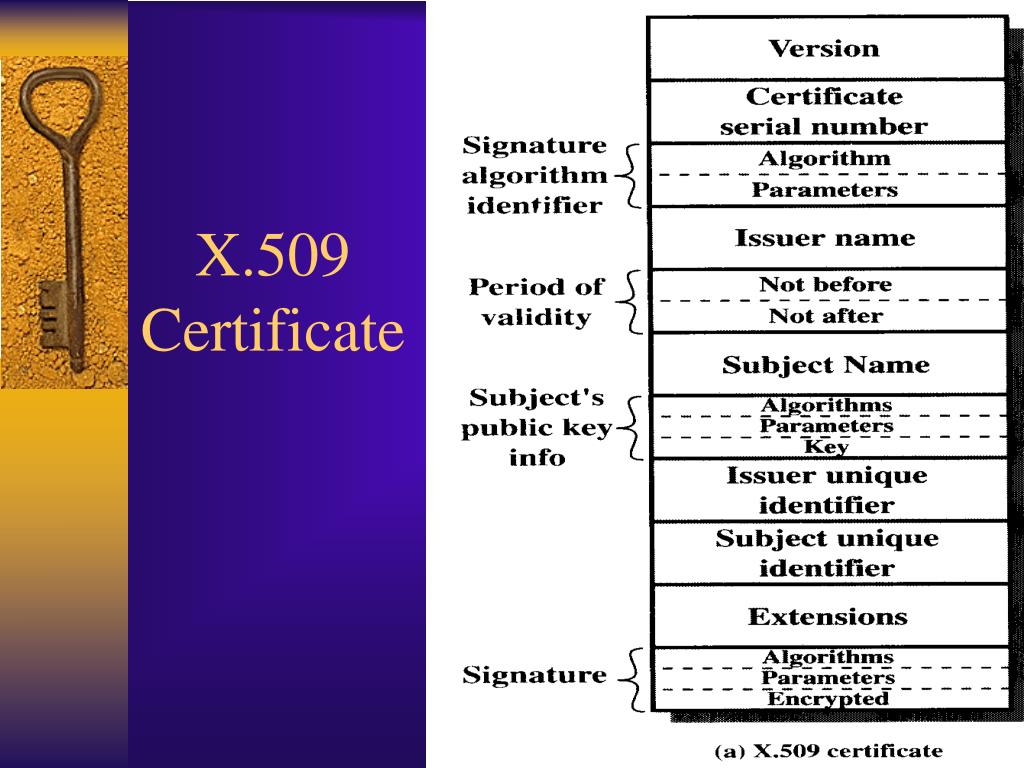
X.509 Certificate Example
If the issuer name is not specified, then the issuer name is set to 'Unknown'. When issuer is 'Unknown', the certificate owner will have to manually get a x509 certificate from the issuer of his/her choice, then merge the public x509 certificate with the key vault certificate pending object to complete the certificate creation.
Partnered CA Providers
Certificate creation can be completed manually or using a “Self” issuer. Key Vault also partners with certain issuer providers to simplify the creation of certificates. The following types of certificates can be ordered for key vault with these partner issuer providers.
| Provider | Certificate type |
|---|---|
| DigiCert | Key Vault offers OV or EV SSL certificates with DigiCert |
| GlobalSign | Key Vault offers OV or EV SSL certificates with GlobalSign |
A certificate issuer is an entity represented in Azure Key Vault (KV) as a CertificateIssuer resource. It is used to provide information about the source of a KV certificate; issuer name, provider, credentials, and other administrative details.
Generate X 509 Certificate From Private Keys
Note that when an order is placed with the issuer provider, it may honor or override the x509 certificate extensions and certificate validity period based on the type of certificate.
Authorization: Requires the certificates/create permission.